I like cracking passwords. Did you ever carefully peel back the wrapping paper on a Christmas present when you were a kid? That little peek at what you weren’t supposed to see is the feeling I get when I know I’ve successfully compromised an account.
Now, full disclosure, as an ethical hacker I only do this when hired by a client who’s given me explicit permission to do so. The technical term is password auditing, but in truth we use the same tools and techniques that a criminal would. And I’m going to share some of those with you.
Computer passwords have always been a lousy form of security; even the computer scientists at MIT who pioneered their use in the mid 1960s knew there were more secure options. Yet here we are, some 50 years later, entrusting our entire digital lives to a technique that was inferior even two decades before IBM introduced the PC. What happened?
In a word, simplicity. Humans have been using passwords in some form or another since antiquity, so their adaption to the realm of technology is no surprise. The early Cold War-era mainframes at MIT had limited resources, and passwords were – computationally speaking – a relatively cheap way to add a small layer of security. There was no shortage of alternatives as technology advanced, but familiarity and a lack of agreement on what should replace it meant the lowly password remained the de facto choice.
Today, of course, we have exponentially more computing power than in the 1960s, but the same amount of brainpower. The practical impact of this is that tasks that used to take a supercomputer – say guessing several thousand passwords a second – can now be accomplished on any low-end machine found in the bargain bin of a thrift store. While our ability to remember long, complex passwords hasn’t increased, the ability to crack them has. The rise of cloud computing means that attackers have more resources now than they could have dreamed of when Intel started World Password Day in 2013.
So as an attacker, how would I leverage all of this power to crack your password? Here’s my quick and dirty top 5 list:
1. Dictionary Attack
The first type of attack I’d turn to is known as a dictionary attack. Simply put, I’ll load a dictionary file into any one of a myriad of password cracking utilities and let it loose on your account.
Some of you are feeling clever right now with something like “pa$$w0rd”. Ditch the hubris – hackers have been onto these tricks since Day 1. The dictionaries we use aren’t coming from Webster’s, but our own custom blends that can account for simple character substitutions or the addition of a number or 3. And if you’re still feeling clever, dictionary files, or wordlists as they’re known in the trade, are readily available in pretty much every language – even Klingon.
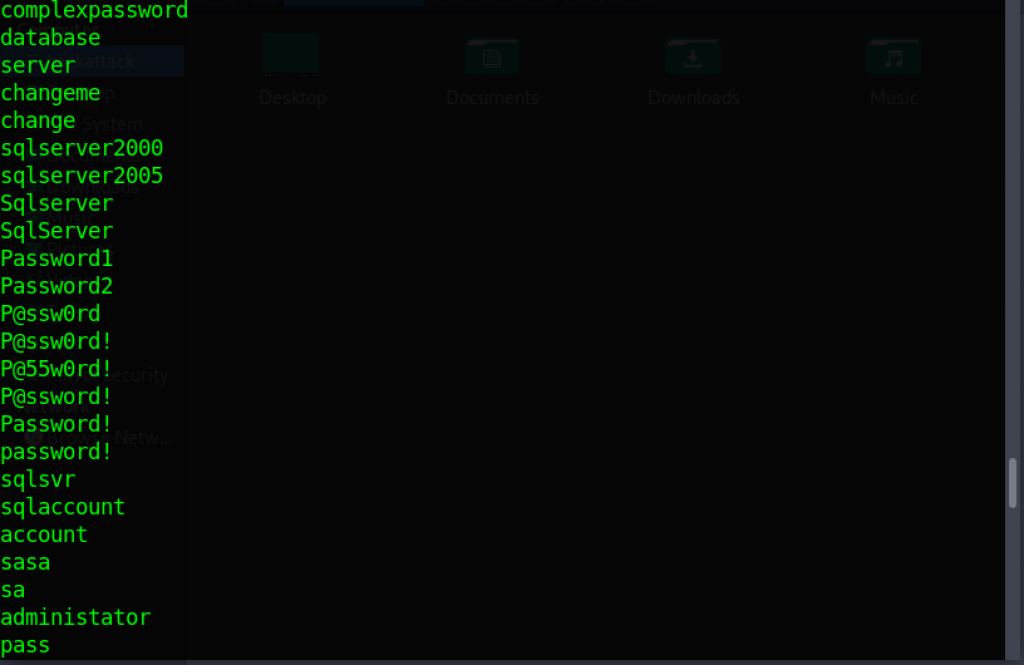
Here’s part of a simple wordlist file for use in a dictionary attack. Any password here would likely be cracked in minutes.
How to stop it: Make sure you’re not using any form of a dictionary word – even with added numbers or punctuation – as your password. A phrase can be better than a word; I can easily crack “p@$$w0rd”, but something like “ILoveGoingToTheBeachOnSundays” is much more difficult. Stringing nonsense together is even safer: “IndigoIndigoEpsilonBearTrap23” is probably never going to get cracked, because there’s no logical relation between any portion of the password, and it’s not a phrase that can be found in any published work.
2. Credential Stuffing
If you re-use usernames and passwords across multiple sites, you’re highly vulnerable to a credential stuffing attack. Thanks to the countless number of data breaches that have occurred in the last few years, most of our account credentials are already out there. Anyone with Internet access can go to https://haveibeenpwned.com right now and download over 550 million leaked passwords in a hashed format. There’s no unique technical skills required here: the site’s database is comprised of known data breaches maintained by security expert Troy Hunt. Hackers of even a basic skill level know where to find even more – think dark web, underground forums, and hidden chat rooms.
All of this means we know the passwords most commonly used, and can quickly throw, say, the top 1000 passwords at an account. We also have a large pool of known username/password combinations we can rapidly try across different web sites and services. You’ve probably already heard of some of the most famous credential stuffing campaigns without even knowing it – think the “hacks” of Ring video doorbells, Nest cameras, Disney+ accounts and more. Because so many people re-use passwords between sites, credential stuffing is a pretty reliable technique. There are even dedicated tools to automate the process.
How to stop it: Never re-use passwords between different web sites. Data breaches are common, and not always widely publicized. If you struggle to remember passwords across a large number of sites, use a password manager like LastPass or 1Password. Enable Multi-factor authentication on all your accounts. Most sites now support some form of it, and while it’s not unbreakable, it provides an exponential increase in security over a password alone. Our favorite is Duo Security (we’re a Duo partner), but there are plenty of other great options, including Google Authenticator and Authy.
3. Social Engineering
In many instances, the easiest way to get your password is to convince you to give it to me. Sound implausible? What if someone called using the number of your company and said they were from the company’s I.T. department, and a cyberattack threatening the entire company was originating from your PC? This works an amazing amount of the time if you insert the right mix of fear, technology, and urgency.
In this type of attack, I’d do a little research first so I could find your company username or ID, and perhaps even adopt the persona of a real employee in your I.T. department. Faking the Caller ID of your corporate headquarters is a relatively easy task that adds extra credibility. Adding something time-sensitive – like an attack in progress – preys on human psychology; the victim has less time to think logically and is more likely to cooperate out of fear.
You don’t even need to be the direct target of a social engineering attack for it to be successful. In 2012, WIRED reporter Mat Honan had his entire digital life erased after hackers used social engineering attacks on customer service agents from Apple and Amazon. If I can convince a customer service rep to e-mail me a password reset link, I can take over your account without ever knowing your password. Here’s an example of just how easy social engineering can be:
How to Stop It: Awareness is the best defense against social engineering. Make sure you and your employees receive security awareness training to spot the latest scams and threats. Free resources are available from multiple sources, including Cofense, ESET, and The SANS Institute. Multi-Factor Authentication (MFA) can provide some protection against social engineering attacks, but is often the targets of such attacks itself. You should never share a password, PIN, or security code with anyone, no matter how convincing they may seem.
4. Phishing

A cybersecurity mentor of mine who’s frequently tasked with testing the security of sensitive government agencies once told me he’s never been on an engagement where phishing didn’t work. Phishing has a number of advantages for an attacker. It’s cheap and easy to implement, and preys on human nature, often bypassing technological safeguards in the process. Even those who’ve undergone security training can be phished with alarming success rates. ZDNet recently reported that a spear-phishing campaign targeting high-level executives netted victims at over 150 companies.
Phishing is also easy to adapt in response to current events; researchers from Barracuda Networks say they’ve seen a nearly 700% increase in coronavirus related e-mail attacks since the end of February. This isn’t particularly surprising given that e-mail attacks typically rely on fear and a sense of urgency to be successful; a global pandemic certainly provides both in spades. With purpose-built phishing toolkits widely available online, virtually any would-be criminal is capable of carrying out this type of attack.
How to stop it: Training and awareness are again the key to fighting phishing attacks. To see how your employees fare, you can use free phishing simulators from KnowBe4, PhishingBox, and The InfoSec Institute. Technical safeguards can filter many phishing emails, but are no substitute for human awareness. MFA can again provide another layer of security, and Duo Security includes a phishing simulator as part of its plans.
5. Default Usernames and Passwords
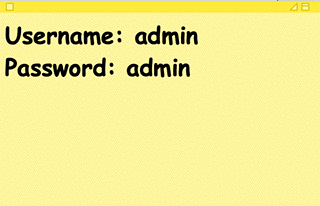 Some vendors are getting smarter about this one, but there’s still plenty of devices and services out there still running with the default credentials they left the factory with. Let’s say I’m interested in intercepting all of the network traffic at a coffee shop that offers free Wi-Fi. It’s fairly trivial to discover the type of equipment the coffee shop is using – say Linksys or Netgear – and then try all of the default logins of that particular manufacturer. An alarming number of users never bother changing this, which presents a huge backdoor. This type of attack also works great against Internet of Things (IoT) devices like cameras and printers, websites running older versions of WordPress, and even a number of corporate applications.
Some vendors are getting smarter about this one, but there’s still plenty of devices and services out there still running with the default credentials they left the factory with. Let’s say I’m interested in intercepting all of the network traffic at a coffee shop that offers free Wi-Fi. It’s fairly trivial to discover the type of equipment the coffee shop is using – say Linksys or Netgear – and then try all of the default logins of that particular manufacturer. An alarming number of users never bother changing this, which presents a huge backdoor. This type of attack also works great against Internet of Things (IoT) devices like cameras and printers, websites running older versions of WordPress, and even a number of corporate applications.
Once I’ve opened a door into a device using this technique, I can use it to launch further attacks. I might use the device to snoop on network traffic, host malware, or redirect legitimate Internet queries to a site of my choosing. Weak default credentials pose such a significant risk that the California legislature banned them in 2018. Still, the law has been laxly enforced, and there are plenty of existing devices out there to exploit.
How to stop it: Always change the default credentials as soon as you set up a new device or service. It doesn’t matter how unimportant that account may seem, it needs to be changed to prevent major security risks.
Enjoyed this post? Sign up for our FREE Small-Business Cybersecurity Newsletter. Once a month, no obligation, unsubscribe anytime.
