
Learn the Secrets of an Ethical Hacker
We take a completely different approach to Security Awareness Training: we’ll help you build a cyber-resilient workforce by constructing a fictional hacking campaign against your company. Our security awareness training program is designed from the ground up to maximize engagement and recall through live instruction, interactive exercises, and real demos. No more PowerPoints and e-Learning modules from 2002. From conducting pre-attack reconnaissance to exfiltrating data, we’ll demonstrate the real tools, techniques, and procedures that cybercriminals use to breach organizations large and small.
82% of Data Breaches in 2022 involved a human element.
-Verizon Data Breach Investigation Report
Building The Human Firewall
Security awareness training is the most cost-effective cybersecurity investment your company can make. Thats because most attacks involve a human element. From Uber to Twitter to the coffee shop down the street, cybercriminals have discovered that targeting human weaknesses rather yields vastly superior results, with less risk of being caught. From stronger passwords to greater vigilance, your organization will gain a new level of resilience at every stage of the Cyber KillChain.

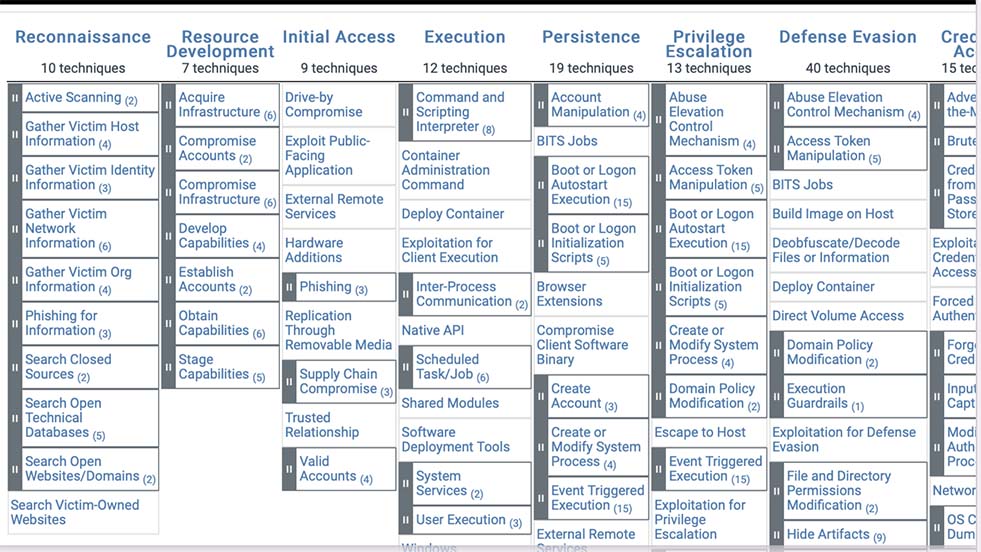


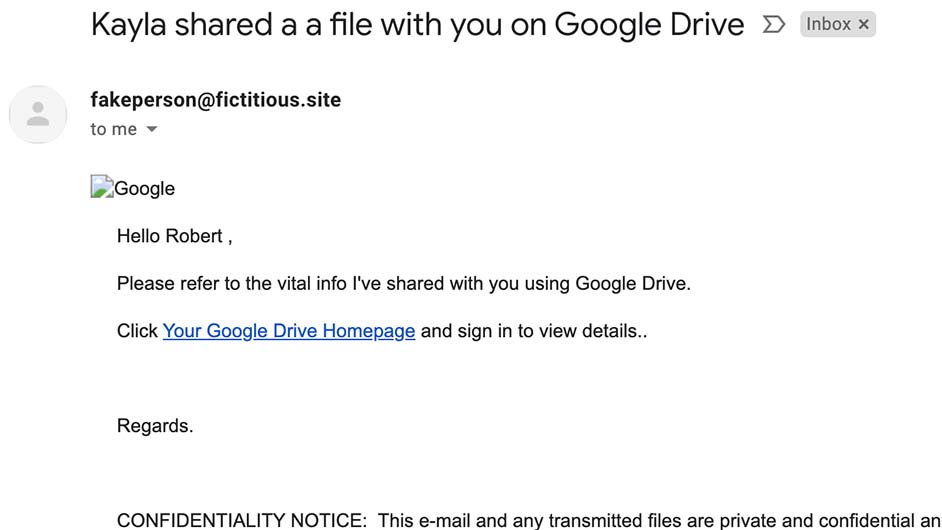
Understanding The Complete Lifecycle of an Attack
Most security awareness training takes a narrow view of specific topics like phishing or password strength, without providing any context. Our program provides unique insights into an attacker’s entire range of activities. We explore how hackers gather information on potential targets, discover how they move laterally once they’ve established a foothold in the organization, and look at how they maximize profits post-breach. The added context helps your employees understand why cyber security measures are important, instead of simply burdening them with additional requirements.
Relevant Knowledge from Real Attacks
We continually update our Security Awareness Training curriculum to reflect the latest tools, tactics, and procedures (TTPs) seen in real-world cyberattacks. From advanced phishing techniques to bypass multi-factor authentication to cloud-based attacks that sidestep antivirus programs, your employees will be left better prepared to identify and respond to signs of the most cutting edge attacks.
Class Topics and Format
Format: Live instruction delivered over Zoom or similar platform. Includes a mix of lecture, demos, and interactive participation. In-person sessions are also available in the greater Long Beach, CA area.
Duration: Typically 12 Hours of training delivered over the course of three days.
Topics Covered:
- Types of cyberthreats and review of recent attacks
- Anatomy of an attack, including an inside look at tools and techniques used
- How hackers gain initial access to an organization (phishing, credential harvesting, malware etc)
- Social Engineering techniques used to target human weaknesses
- Actions carried out after initial access (lateral movement)
- Data Exfiltration and other ways for attackers to. profit (extortion, ransomware, etc)
- Best practices and ways to defend against attacks
- Plenty of opportunities for Q&A along the way!