Twitter has long known its a hacking target. Last year Twitter CEO Jack Dorsey temporarily lost access to his own account after attackers targeted his phone carrier. Access to “OG” Twitter handles like @greg or @kc are regularly traded on underground hacker forums. The company has a dedicated Detection and Response Team to handle security incidents, as well as various mechanisms to thwart potential attackers.
So how did a teenager from Florida takeover some of the world’s most followed Twitter accounts, including those of Barack Obama, Joe Biden, Elon Musk, Bill Gates, Jeff Bezos, and others? And what we learn from Twitter’s breakdown in security? Here are some of the most important lessons, based on what we know so far:
The Hack
Based on court filings in the pending criminal case, we know that the Twitter hack began with a phone call to a Twitter employee. That employee thought they were talking to a member of the company’s IT department, but the voice on the other end of the line was really 17-Year Old Graham Ivan Clark of Tampa, Florida. Clark successfully talked the Twitter employee into providing a set of user credentials that provided a path into the social media giant’s internal systems.
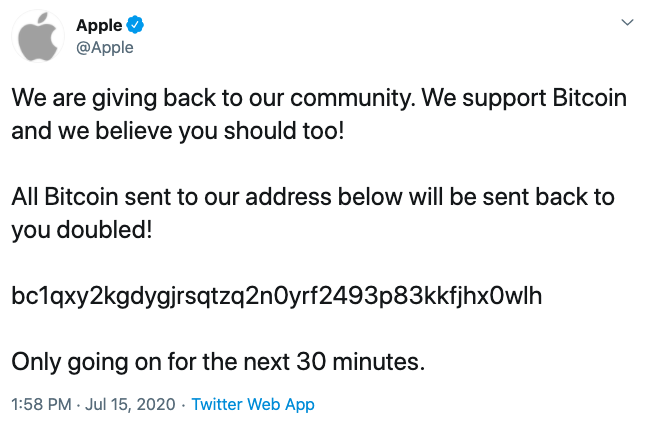
The initial account Clark gained access to did not have access to internal support tools used by Twitter employees to reset passwords and e-mail addresses associated with Twitter accounts. But it did give the teenager a window into the company’s internal procedures, processes, and personnel. Armed with this knowledge, Clark and perhaps other perpetrators, carried out additional attacks to gain control over accounts that did have access to Twitter’s internal support tools. The attackers then used these tools to change the e-mail addresses associated with dozens of high-profile accounts. The result was that a password reset request for say, @JoeBiden or @ElonMusk ended up going to Clark’s inbox instead of the rightful owner. It appears Clark then sold access to these accounts to accomplices, who then launched a BitCoin scam that tipped off Twitter, and the world, to the attack.
Lesson 1: Humans Are The Weakest Link
This attack relied on a significant and concerted attempt to mislead certain employees and exploit human vulnerabilities to gain access to our internal systems.
-Twitter Statement, July 31, 2020
It’s very important to note that the initial entry point was a human failing, not a technical one. Clark didn’t break through firewalls or use hacking tools to crack passwords; he simply called up an employee and asked for what he needed.
As a simple analogy, picture a safe. A locking mechanism, no matter how advanced, isn’t going to do much good if a thief can convince the safe’s owner to reveal the code. Likewise in the digital arena, compromising a human can bypass some of the most effective technical controls. This appears to be more or less what happened to Twitter.
The lesson we should take from this is that investing in technology alone isn’t sufficient; we need to make sure all of our human employees receive at least a base level of security awareness training. Some of our favorite platforms for quality training include Habitu8, KnowBe4, and Ninjio.
Lesson 2: Secure Your Passwords
According to ZDNet, Clark’s initial access may have been to a Twitter Slack channel that contained credentials for the company’s support tools. Again, the principal failing here is a human one and not technical. If your internal administrator passwords are posted in plain sight, there’s really no need to do any kind of real hacking. Think of a car thief; why would they hot-wire a car if the keys are left in plain sight?
Unfortunately, far too many organizations leave important usernames and passwords in a place where they are easily accessible. In the case of Twitter, that was a Slack channel, but other easily accessed targets include Word files, emails, and even GitHub repositories. The ultimate sin is a post-it note stuck to a computer monitor.
If you or your employees are having trouble remembering a myriad of different passwords, a good option is to use a password manager like LastPass or 1Password. We recommend against using the password manager built into your web browser, as they don’t store the information as securely.
Lesson 3: Adversaries Do Their Homework
By the time Clark carried out his series of attack on July 15, he’d gathered enough information to know exactly which Twitter employees to target. This was likely the result of weeks or even months worth of research. The phone scam that gave Clark his first steps into the company’s network may have happened as early as May 3. He then managed to lurk for months undetected in Twitter’s network, gathering information that would be used later.
This may seem unusually sophisticated for a teenager, but it’s common for attackers of all types to spend a great deal of time performing reconnaissance on their targets. Often, attackers will glean information from the public domain before ever attempting to breach their target.
LinkedIn profiles, for example, are tremendously valuable for gathering information on company personnel. A talented social engineer might choose to target recent hires who are more easily intimidated or tricked. Or, they may find a real employee from the I.T. department and impersonate them in a phone attack like the one Clark used against Twitter.
Even job postings can be great source of intel for a resourceful attacker. Often, companies will state their preference for candidates that have experience with particular products or systems, sometimes going so far as to specify a particular version. Hackers can then be reasonably sure that product/system is in use at the target organization, and tailor their attacks accordingly. Take a look at this real example:

If we were an attacker, we might use this information to target known vulnerabilities in Windows Server 2012, SonicWall VPNs, or Microsoft Office apps.
Lesson 4: 2FA Isn’t Foolproof
The attackers successfully manipulated a small number of employees and used their credentials to access Twitter’s internal systems, including getting through our two-factor protections.
-Twitter statement, July 18, 2020
In the immediate aftermath of the Twitter attack, some questioned why the social media giant wasn’t using two-factor authentication (2FA) to protect its internal accounts. 2FA is one of the best ways to protect your accounts because it requires more than a simple username and password combination. But like everything else in life, 2FA isn’t foolproof.
In a public statement three days after the attack, Twitter confirmed it was using 2FA to protect its administrative accounts. So what happened? Based on the limited information available, it appears Twitter’s 2FA implementation was based on one-time codes delivered through either an app or text message. Clark’s social engineering skills were so good that he was apparently able to convince Twitter employees to reveal these codes over the phone.
This type of attack should have been well known to Twitter: just over a year ago, CEO Jack Dorsey had his account taken over through a similar type of attack called SIM swapping. Essentially what this means is the attackers convinced customer service reps at Dorsey’s cellphone carrier to change the SIM card associated with his phone number, allowing them to receive the 2FA codes.
This should be very concerning, as most banks, financial institutions, and other high-value targets default to using codes sent to a mobile number. SIM Swapping has proven an effective attack in bypassing 2FA, and wherever possible you should be using an authenticator app like Duo or Authy. Twitter’s own response in the wake of the July attack goes a step further, using physical hardware tokens like those made by Yubikey. While costly, hardware tokens provide the maximum amount of security, as an attacker would need to gain physical access to the token to compromise an account.
Lesson 5: Your Vendors and Business Partners are an Attack Vector
There is absolutely nothing Apple, Bill Gates, Elon Musk, or Barack Obama could have done that would prevented their Twitter accounts from being taken over on July 15; the failure was internal to Twitter. This illustrates that its possible to do everything right and still be compromised anyway. Business partners and third party vendors are a blind spot that too many companies fail to consider when creating a cybersecurity strategy.
Perhaps no one has felt this lesson more deeply than Target. In 2013, a phishing email delivered to an employee at a third-party refrigeration contractor kicked off a series of events that ultimately led to the credit card and personal details of 110 million Target customers falling into the hands of criminals. Target shares plenty of plenty of blame for failing to secure its own network, but the initial access was a business partner, not the bullseye itself.
The lesson to be learned here is that you need to do more than make sure your own house is in order; you have to check up on your vendors, contractors, and suppliers as well. Anyone that processes data or provides a service to your business is a potential attack vector.
As always, following good “cyber hygiene” practices – implementing best practices like strong passwords, the principle of least privilege etc. – is the best way to thwart potential attacks.
If you’d like help implemting any of these lessons for your business, please don’t hesitate to contact us today!
